BROWSER AND WEB SECURITY
Browser Protocols
Web browsers will use at least the basic HTTP (Hypertext Transfer Protocol) to open web pages using a URL (Uniform Resource Locator), e.g. http://www.example.com. We will ignore the other protocols such as FTP (File Transfer Protocol) and the difference between URL and URI (Uniform Resource Identifier ). However, the use of HTTP does not provide any effective security between the browser and the website. To accomplish this, HTTPS (HTTP Secure) requires the authentication of the visited website and facilitates protection of the privacy and integrity of the exchanged data. This originally was accomplished by using an SSL (Secure Sockets Layer) protocol and later using the TLS (Transport Layer Security) protocol. These protocols overlapped and, although the SSL term is still in use, the earlier versions have been deprecated the latest version has been declared not secure, because of a vulnerability. TLS 1.1 is also deprecated and was replaced by TLS 1.2. Now we have TLS 1.3, published on 10 August, 2018, ten years after TLS 1.2 was published.
Although web browsers, Google Chrome (including the Android version) from version 67 onwards, and Mozilla Firefox from version 61 onwards, already have support for TLS 1.3 by default. The latest version (54) of Opera also supports it, although it needs to be specifically enabled. Apple has already implemented draft support for TLS 1.3 in both MacOS 10.13 and iOS 11, although this also needs to be specifically enabled. Because TLS 1.3 has existed in many versions, Microsoft does not yet support it on any of its operating systems or in the Edge and Internet Explorer browsers, because of the need to wait until the specification was finalized. Because of its importance it is expected to be supported soon.
To implement a security protocol requires the certification and validation of the website by a CA (Certification Authority). The installation of a globally trusted TLS server certificate will then show a URL as https://www.example.com.
http://www. https://www.
With the HTTPS protocol, the browser will show a padlock with the URI. It is essential that any website requiring the entering of personal and private data especially data such as credit card numbers and financial information must have this protocol installed. Many browsers display the following symbols and advise that HTTP connections are not secure. In Chrome version 69 (September, 2018), the green colour has changed to grey, similar to Microsoft Internet Explorer 11 and Edge.
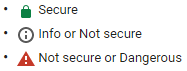
There is a growing movement to have all websites use SSL/TLS, but cost is a factor in its adoption, where it is not mandatory. The issue of a certificate requires several steps to confirm the validity of the website and the credentials used to operate it. Certificates are usually renewed each year and Certification Authorities vary in their charges.
Note: SECURE MAY NOT MEAN SAFE!
Last year information was published showing that in the Chrome browser, having a secure connection does not necessarily mean that it is safe. This is extremely important issue for people who have dealings with Google, Microsoft, Apple and other well-known companies. Phishing websites have managed to obtain certificates by having the certificate hide their site under a name using a domain of a well-known company. After complaints are lodged and the deception confirmed, the certificate will be revoked. However, the problem doesn’t stop here, because the Google Chrome list of safe sites is not updated in real time and the browser will continue to show the site as secure, until the list is updated. This is an ongoing issue and, to understand how it happens, we recommend reading the Wordfence article. We are checking the status of this issue and will update the information soon.
Computer Protection
For those using Microsoft Windows operating systems, we suggest the following procedures to reduce the chance of virus and other malware infections:
- Do not use an unsupported operating system.
- Keep the operating system updated with all security downloads.
- Use Microsoft Security Essentials, Windows Defender, or other free antivirus programme such as Avast and activate the appropriate firewall. Be warned that some free antivrus programmes may create more problems than they solve. Good comprehensive antivirus programmes are offered by companies such as Symantec™, McAfee™, and Kaspersky™.
- Udpate the virus definitions daily.
- Uncheck SSL 3.0 protocol on your browser settings.
- Avoid sites that have aggressive advertising and unlikely offers. Reduce unwanted advertising by installing an ad-blocking programme such as Adguard. This will reduce the bandwidth and save you money, when using paid mobile data connections.
- Avoid using open, unsecured WiFi connections.
- On your WiFi router, change the default Admin log-in name and password. Whenever it is possible, use a router that supports the WPA2 Personal (WPA2-PSK) protocol. Choose an SSID (service set identifier) name, set the encryption type to AES and create the password, or network key, for the encrypted Wi-Fi and activate its firewall.
Home Routers
On 11 April, 2017, we learned from Wordfence that half of the ISPs (Internet Service Providers) analyzed have routers with a very specific vulnerability. This vulnerability is known as the “misfortune cookie” or MC vulnerability for short. It has been known for a few years and was first disclosed by CheckPoint in 2014. It is now being used to hack home routers via port 7547. Using a scanning tool below you can tell if you have the MC vulnerability. If you would like to know more about this problem and check your home or other router to which you are connected, you can visit the Wordfence page to learn more about the steps you can take, if your router is vulnerable. We found that our router was vulnerable and we closed port 7547, after giving up attempts to have our ISP attend to the problem.
Ransomware Attacks.
On 12 May, 2017, we learned of massive ransomware attacks that spread to more than 200,000 computers in 150 countries in the first 2 days. It was stopped, but has started again. There are different types of ransomware. However, all of them will prevent you from using your computer normally and they will all ask you to do something before you can use your computer or access files. Ransomware can prevent you from accessing Windows, or can encrypt files, so you can’t use them. It may stop certain applications like your web browser from running. Ransomware will then demand that you pay a ransom to get access to your PC or files. However, there is no guarantee that paying, or doing what the ransomware tells you, will give access to your computer or files again.
This particular ransomware only affects computers using Windows versions prior to Windows 10. Windows 7 and 8.1 are still supported by Microsoft and a security update for this vulnerability was released on 14 March, 2017. If you update regularly you will already have the security patch on your Windows 7 or 8.1 computer. If not, update now! Windows XP, Vista and 8.0 are no longer supported. If you use Vista, since the patch for Vista should have been issued before support stopped on 10 April, you may be lucky, but read further. There are probably still more than 100 million users of Windows XP around the world and because of the seriousness of this particular issue, Microsoft has issued out-of-band security patches for Windows XP, Vista and 8.0. If you are using one of these versions, you can get the relevant patches from Microsoft Update. Do it before it’s too late!
On 28 June 2017, another ransomware known as Petya, starting in the Ukraine attacked companies and government offices and spread internationally. This ransomware is exploited a vulnerability in Microsoft Office, when handling RTF documents (CVE-2017-0199). It also exploited a vulnerability in SMBv1, which is the Microsoft file-sharing protocol. This second vulnerability is described in Microsoft security bulletin MS17-010. Computers may have already received patches from Microsoft back in March, but after a few days, a vaccine was found. You can download a batch file from the following link: https://download.bleepingcomputer.com/bats/nopetyavac.bat and run as Administrator.
Severe Vulnerability in All Wi-Fi Devices
A major Wi-Fi vulnerability that has been named “KRACK” was announced on 16 October, 2017. This affects absolutely every device that supports Wi-Fi. The vulnerability allows attackers to decrypt WPA2 connections. Note that WPA2 is the most secure protocol available for Wi-Fi.
Researchers have discovered a way for an attacker to read sensitive information that is sent over a Wi-Fi network using WPA2 and attackers can use this to steal sensitive information like credit card numbers, passwords, chat messages, emails, photos and more. It may also be possible for an attacker to inject malicious information into the Wi-Fi network. This could include ransomware and malware.
The vulnerability is in the Wi-Fi standard itself, and not in individual products or their implementations. That means that all products that correctly implement the WPA2 standard are affected. If your device supports Wi-Fi, it is likely affected by this vulnerability. Products that are known to be affected by this at this time include Android, Linux, Apple, Microsoft Windows, Linksys, D-Link, Netgear and many more. The list of affected products is enormous and vendors including Amazon are scrambling to release patches to fix this issue. The devices and hardware you will need to update, once patches are released, include the following:
- Desktop workstations
- Laptops/notebooks
- Mobile phones
- Tablets and e-readers that use Wi-Fi
- Home and office routers
- Home devices like NEST, Amazon Echo and Google Home
- Printers, both home and office, that use Wi-Fi
- Any other device that uses Wi-Fi
Keep your eyes open for firmware and software updates and, in the meantime, avoid using Wi-Fi connections for sending sensitive data, especially with Linux computers and Android phones which have the greatest vulnerability.
The above information about this Wi-Fi vulnerability has been summarized from information published by the Wordfence organization and was checked against information provided by the US Government CERT Coordination Center.
Meltdown and Spectre Side-Channel Vulnerability
On January 3, 2018, the NCCIC (National Cybersecurity and Communications Integration Center) became aware of a set of security vulnerabilities, known as Meltdown and Spectre, which affect modern computer processors. These vulnerabilities can be exploited to steal sensitive data present in a computer system’s memory. Spectre affects almost all devices including desktops, laptops, cloud servers, and smartphones.
CPU hardware is vulnerable to side-channel attacks, referred to as Meltdown and Spectre. Meltdown is a bug that “melts” the security boundaries normally enforced by the hardware, affecting desktops, laptops, and cloud computers. Spectre is a flaw an attacker can exploit to force a program to reveal its data. The name derives from “speculative execution”, which is an optimization method a computer system performs to check whether it will work to prevent a delay when actually executed.
In the case of Spectre, the vulnerability exists in CPU architecture rather than in software, and is not easily patched; however, this vulnerability is more difficult to exploit.
Because the vulnerabilities can affect hardware and software in many different ways, users and administrators should refer to their hardware and software vendors for the most recent information. After patching, the impact on performance may vary, depending on use cases.
Typical antivirus programs are built on a signature management system, and may not be able to detect the vulnerabilities. You should check with your antivirus vendor to confirm compatibility with Meltdown and Spectre patches. We are aware of problems that occurred after updating Microsoft software caused by requirements change registry settings. The updates failed until the required changes were made. Microsoft recommended third-party antivirus vendors add a change to the registry key of the machine running the antivirus software. Without it, that machine will not receive any of the following fixes from Microsoft:
Windows Update, Windows Server Update Services and System Center Configuration Manager.
More information can be found here: https://support.microsoft.com/en-us/help/4072699/january-3-2018-windows-security-updates-and-antivirus-software.
Microsoft admitted to vulnerability-related Windows slowdowns and initially paused distribution of its Meltdown and Spectre patches for certain AMD processors because the updates were causing fatal errors in some machines – yes we experienced that!
1 March, 2018. Microsoft is planning to distribute Intel’s firmware updates to protect Windows 10 systems against the Spectre CPU vulnerability. Microsoft is now planning to list the Intel firmware updates in its Microsoft Update Catalog. “We will continue to work with chipset and device makers as they offer more vulnerability mitigations,” says John Cable, from Microsoft’s Windows Servicing and Delivery team. While Microsoft isn’t committing to automatically pushing these firmware updates to the company’s Windows Update system, even listing them in the company’s Update Catalog is a step further than usual. Microsoft says it has also been working with third-party antivirus companies to ensure firmware patches and Windows updates are compatible with systems. There’s a risk of compatibility issues, and because of that Microsoft is requiring that antivirus programs mark that they’re compatible before updates are applied. Presumably Windows 7 users can check the WU catalogue.
1 March, 2018. Microsoft is planning to distribute Intel’s firmware updates to protect Windows 10 systems against the Spectre CPU vulnerability. Microsoft is now planning to list the Intel firmware updates in its Microsoft Update Catalog. “We will continue to work with chipset and device makers as they offer more vulnerability mitigations,” says John Cable, from Microsoft’s Windows Servicing and Delivery team. While Microsoft isn’t committing to automatically pushing these firmware updates to the company’s Windows Update system, even listing them in the company’s Update Catalog is a step further than usual. Microsoft says it has also been working with third-party antivirus companies to ensure firmware patches and Windows updates are compatible with systems. There’s a risk of compatibility issues, and because of that Microsoft is requiring that antivirus programs mark that they’re compatible before updates are applied. Presumably Windows 7 users can check the WU catalogue.
We will be happy to advise on the implementation of information technology security measures for home or office.
 TRANSAPEX WEBCOM
TRANSAPEX WEBCOM